Some of you might wonder in which situations an SSL certificate should be used. This tutorial will help you find an answer to whether or not you should upgrade your website or anything else by adding encryption.
The most important parts of a certificate are the public key and the private key.
The following image shows you what happens when a client tries to establish an encrypted connection to some webserver.
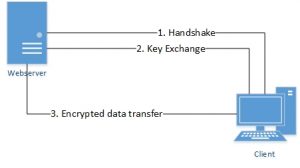
First, the client contacts the server and offers available encryption types, and the server and the client come to an agreement on which type to use.
The web server sends the public key to the client so the client will be able to encrypt its requests. The web server got his private key to decrypt all encrypted client requests. With the private key, you can decrypt all client requests which were encrypted with the public key, that is why you should never hand out your private key to any third party.
To show you the advantage of using encryption, we created an HTML page containing a simple form that can be found on many websites. In the text fields we entered a username and password.
The username we chose: [email protected]
The password we entered: "unencryptedpassword"
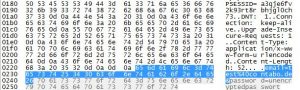
To show the difference between encrypted and non-encrypted messages, we captured some packets using a networking tool.
Without any encryption we could easily extract the username and password used, and we could also see which sites we visit.
With encryption enabled, we could not find either a username or password.
It just shows a packet containing some encrypted data, without the private key we cannot determine which data was actually sent.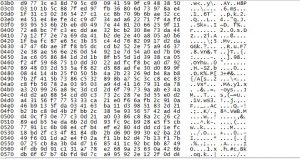
If you are running a website, an email server, or just an FTP server, it is always up to you to offer encryption or not. Offering encryption to your customers is the best way to act professionally.
There are many types of encryption, this post just handles certificates. Usually, encryption algorithms have not changed for years, if you are going to optimize your server you will of course have to think about encryption types, etc.
The real meaning of those connection warnings:
If you are running a web interface (cPanel, Plesk, Webmin, etc.) you probably encountered a warning as follows:
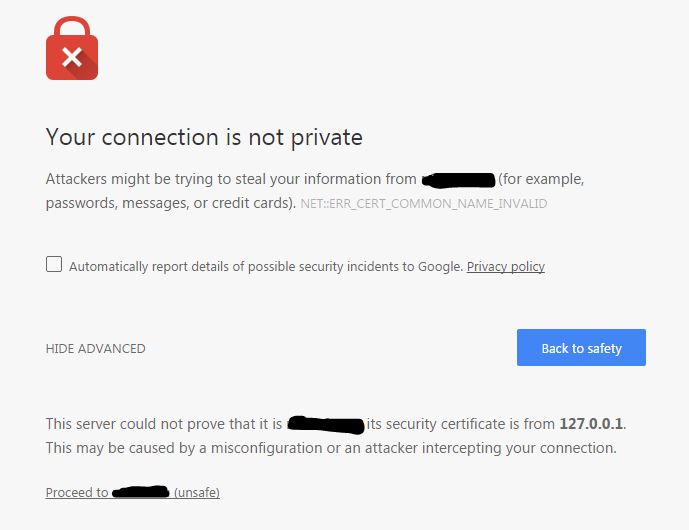
"The connection is not private", usually you should rethink if you really want to proceed. There is the possibility that some server got hijacked and you are redirected to the wrong website. In this case, the warning pops up because the certificate is not valid for the domain we entered. On a web interface, you will get a similar warning when using a so-called "self-signed certificate". Your browser has a list of authorities that it will trust, signed certificates by one of those authorities will not show any warning.
It can be really unwanted if that warning is showing to all of your customers, sometimes this warning is misinterpreted and the website will be left.
There is only one way to remove this warning, you need to get a certificate signed by some official authority.
Some official authorities, such as "Let's Encrypt", will sign your certificate for free, this is a nice option but not really recommended in a production environment. Usually, the domain-validated certificate or wildcard certificate is being used for a production environment, those certificates usually are valid for 365 days (1 year).
There are some differences between single-domain, multi-domain, and wildcard certificates. Usually, you would want a certificate for "yourdomain.tld" or "www.yourdomain.tld". A single-domain certificate will be valid only for one of those domains, a multi-domain certificate alias UCC (Unified Communications Certificate) is valid for all domains included within that certificate. In case you want "www.yourdomain.tld", "yourdomain.tld" and "subdomain.yourdomain.tld" within a single certificate, a UCC should fit your needs.
There is also some extended validation available, some bigger companies take advantage of this (e.g. PayPal ![]() ). At this point I want to mention that the private key and certificate will always remain the same, there is no encryption change, and the certificate will just get signed.
). At this point I want to mention that the private key and certificate will always remain the same, there is no encryption change, and the certificate will just get signed.
Right after you get your certificate signed by some official authority, everyone will be able to access your encrypted website without any warning.
Important:
Encryption is important, all services (email server, FTP server, web server, etc.) running on your server should offer a way to establish an encrypted connection. There is no need to install a signed certificate on each service, for most services self-signed certificates are fine.





